How we do it
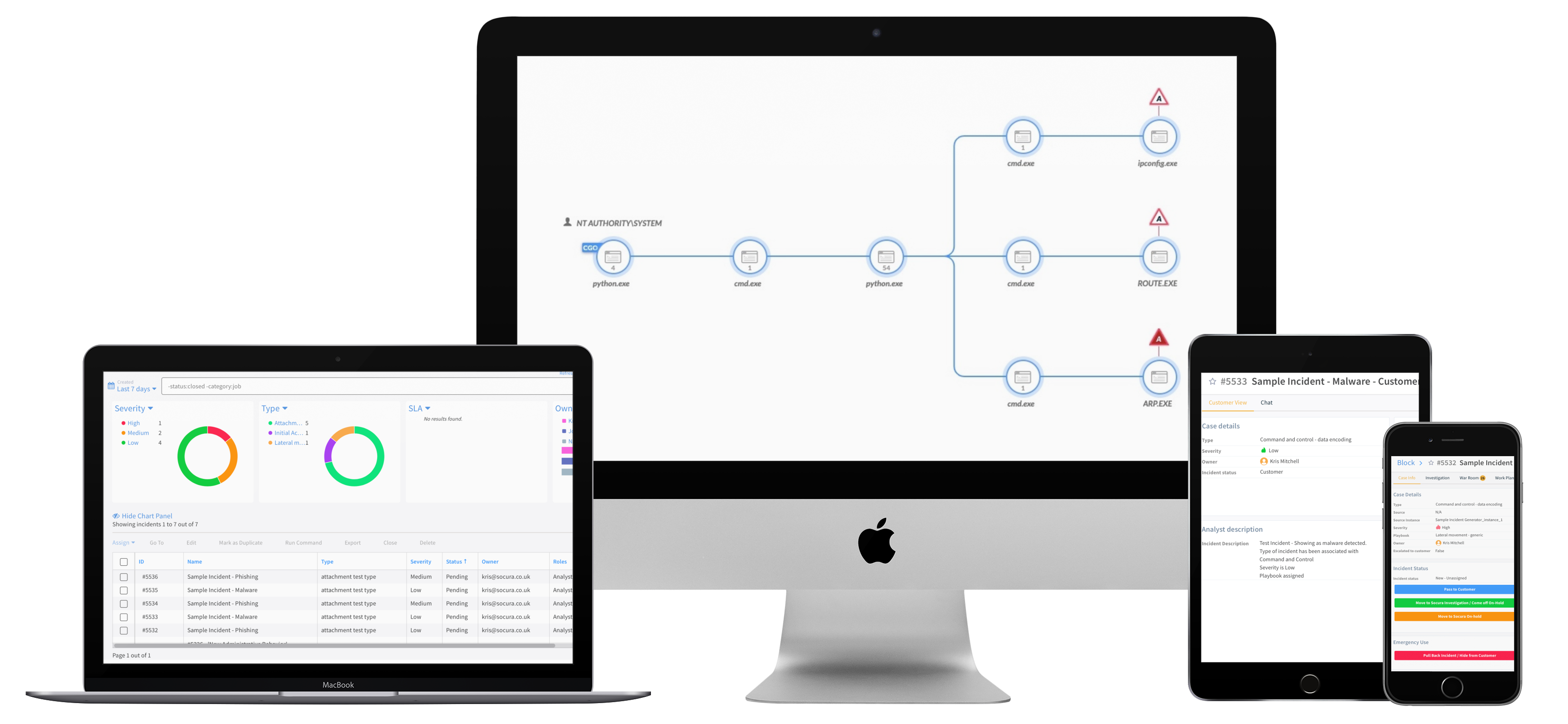
Socura’s Managed Detection and Response service
Our MDR service offers a 24/7 proactive threat detection, hunting and response capability that identifies and contains cyber threats in near real-time.
The service is designed to protect organisations of all sizes from data breaches, reduce attacker dwell time, and negate the impact of any malicious activity on your business operations. To make this happen, we must collect the right data at the right time – with no compromises.
We will consume all of your security telemetry, with no limit on volume, and use the latest advancements in security analytics technology combined with a highly skilled and experienced team to analyse your data, identify what’s bad, and take action to stop it.
Learn more about the core pillars of our service below:
Expert Analysts
Our people-centric approach is what sets Socura apart. Technology can only take you so far and legacy approaches of building centralised SOC environments can greatly restrict the analyst talent pool available based on their proximity to a specific geographic location. In an industry where experienced SOC analysts are in short supply, compromises are made.
At Socura we’ve tackled this head-on by building a nationally distributed, fully remote SOC environment in which we can recruit the best talent from any location. This optimises the experience for team members and clients alike and frees us to select, train and mature the best talent in the industry.
Our service has been collaboratively architected, combining our technical expertise and industry experience with contribution and feedback from our client base to make sure we’re delivering optimal value and tackling those real-world organisational pain points.
XDR
Extended Detection & Response (XDR) helps us accelerate investigations by providing a complete picture of each incident. It stitches different types of data together (endpoint, network and cloud) and reveals the root cause along with a timeline of alerts, allowing our analysts to perform swift triage. Tight integration with enforcement points lets us respond to threats quickly and apply the knowledge gained through our investigations to detect similar potential attacks in the future.
Not sure about some of the terms, check out our glossary.

True Orchestration and Automation
Built from the ground up on a security orchestration, automation and response (SOAR) platform, our MDR service benefits from simplified security operations by unifying case management, real-time collaboration, threat intelligence management, and automation of containment actions.
Our team is able to manage alerts from any source, standardise processes to act upon those alerts using playbooks, act upon threat intelligence, and automate response for any security use-case. Our clients can interact with live incidents and work collaboratively with the Socura team to minimise the threat and secure their environment.
Security Analytics + Unlimited Log Ingestion
As enterprise infrastructure evolves from on-premises to cloud, sufficient coverage and visibility have emerged as critical barriers to effective threat detection & response. Growing infrastructure, more applications, and more security tools have resulted in data volumes that are higher today than ever before
This has meant that significant infrastructure investment has been needed to enable scalable and swift analysis of security-relevant data. Mean Time to Detect (MTTD) threats and Mean Time to Respond (MTTR) to threats – key security metrics – suffer without this capability.
Conversely, security analytics pricing models have traditionally been based on volume, incentivising you to limit the collection and analysis of security-relevant data, therefore reducing your threat visibility.
With Socura’s MDR service, there are no such compromises. We can ingest all of the security data that your systems generate, resulting in complete visibility across all relevant data sources. This data is retained for 12 months, whilst remaining hot and searchable in milliseconds, meaning we can also instantly and retroactively match newly discovered indicators of compromise against your entire historical telemetry dataset.

